Listen to this article
Cryptographic election flaws can lead to significant setbacks, as demonstrated in the recent incident involving the International Association for Cryptologic Research (IACR). When an official lost their encryption key, the election results became inaccessible, highlighting the vulnerabilities of electronic voting systems. These cryptographic failures remind us of the critical importance of secure key management and the potential impact of encryption key loss on democratic processes. Moreover, experts in cryptographic research emphasize that human errors often play a considerable role in these setbacks, raising concerns about trustee key management practices. The IACR’s experience serves as a cautionary tale for organizations employing cryptographic methodologies in their electoral processes.
Flaws in secure voting mechanisms, particularly those involving cryptography, can undermine the integrity of elections, as recently reflected in the proceedings of the IACR. The unintended loss of an encryption key meant that election results remained hidden, showcasing a serious issue within the realm of electronic ballots. This incident brings to light the challenging balance between technology and human involvement, as mistakes in key handling can lead to operational failures. Additionally, the field of cryptographic studies continues to evolve, pushing for better strategies in trustee key management to prevent future mishaps. As organizations strive to maintain the security of their electoral systems, it is essential to address the common pitfalls that can arise from the integration of advanced cryptographic techniques.
Understanding Cryptographic Election Flaws
Cryptographic election flaws can significantly impact the integrity of a voting process, especially in cryptographic systems utilized by organizations like the International Association for Cryptologic Research (IACR). When key management protocols fail, as they did in the recent leadership election, the entire election can be compromised, necessitating rescinded results and new elections. The reliance on multiple trustees to carry segments of an encryption key adds a layer of complexity to the voting process, which, if improperly handled, can lead to devastating consequences like the loss of access to vital election outcomes.
The case of the IACR underscores the importance of robust key management strategies in safeguarding the electoral process. Human error was the linchpin in this situation, emphasizing that even the most secure cryptographic systems are vulnerable when operated by people. Effective trustee key management, alongside stringent procedures, could help mitigate risks associated with key loss or mishandling, potentially safeguarding future elections from similar failure.
Implications of Encryption Key Loss in Elections
The loss of an encryption key can lead to significant ramifications for an organization’s electoral integrity and decision-making process. For the IACR, losing the crucial key meant that results could not be verified or disclosed, ultimately leading to confusion and distrust among members. This incident illustrates how encryption key loss not only hinders transparency but can also damage an organization’s credibility, putting the efficacy of their electronic voting system under scrutiny.
To address such vulnerabilities, organizations are now prioritizing secure key management protocols. Innovations like the ‘2-out-of-3’ threshold system, where the combination of keys from multiple trustees is necessary to decrypt data, can enhance security and trust. Such measures are integral to ensuring that human error does not derail the voting process in future elections, thus restoring confidence in electronic voting systems.
Enhancing Electronic Voting Systems with Robust Protocols
Electronic voting systems, like Helios utilized by the IACR, have transformed the election landscape but are not without their challenges. The successful operation of such systems necessitates comprehensive planning around cryptographic research and development as well as agile response protocols in case of key management mishaps. By reinforcing the inherent safeguards, organizations can significantly decrease the likelihood of failures that arise from human errors during the voting process.
Implementing structured protocols through which trustees manage their keys is critical. The IACR’s approach to streamline its procedures reassures voters of the integrity and transparency of the election process. Continued investment in both technology and procedural enhancements will ensure that the lessons learned from the key loss incident translate into improved electoral frameworks that uphold democratic values in cryptographic systems.
The Role of Cryptographic Research in Voting Integrity
Cryptographic research plays a pivotal role in ensuring the integrity of electronic voting systems. Organizations like the IACR are at the forefront, exploring ways to bolster security and minimize the impact of human error. With ongoing advancements in encryption techniques and key management practices, researchers are continuously working to refine methods that can prevent scenarios like key loss from occurring in the first place.
Moreover, fostering collaboration between cryptographers, election officials, and key management specialists is essential to producing a robust framework for electronic voting. By leveraging knowledge from research, practical applications in real-world elections can be improved, leading to a more secure and reliable voting experience for all participants.
Trustee Key Management: A Vital Component in Secure Elections
Effective trustee key management is crucial in securing electronic voting systems. The incident involving the IACR highlights these management practices’ significance, as the failure to safeguard individual key fragments jeopardized the electoral process. Having a clear understanding of responsibilities, limits, and protocols for trustees is essential in averting potential key loss that can lead to uncertain election outcomes.
Organizations must not only select trustworthy individuals for these roles but also provide comprehensive training on secure key practices and stringent operational guidelines. By establishing well-defined protocols and checks, the risk of key mismanagement can be significantly reduced, ensuring that all segments of the voting key are safeguarded throughout the process.
Strengthening Election Processes Post-Crisis
In the aftermath of the recent key loss incident, organizations are compelled to revisit their election processes critically. This provides an opportunity for institutions like the IACR to strengthen their electoral frameworks significantly, focusing on prevention strategies and crisis communication protocols. Engaging stakeholders in discussions about refining election integrity can yield beneficial changes that rectify past mistakes.
Implementing feedback mechanisms and transparency within the election process is paramount for rebuilding trust among members. By sharing details on the adjustments made and demonstrating commitment towards accountability and continuous improvement, organizations can restore confidence in their electoral procedures.
Technological Innovations in Voting Security
Technological advancements in cryptography and electronic voting are constantly evolving to meet the needs of secure elections. Innovations such as advanced encryption methods and secure multi-party computation are being utilized to ensure that votes remain confidential while also allowing for transparent counting and verification. These emerging technologies are a testament to the commitment of organizations like the IACR to maintaining integrity in their election processes.
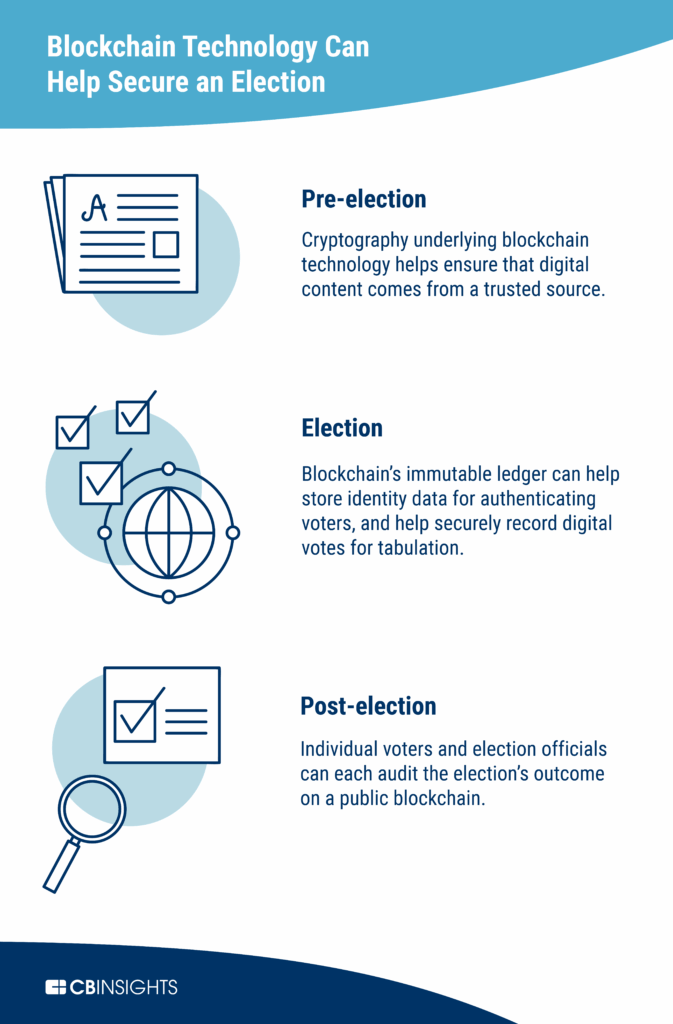
Adapting new technologies can provide a fortified safety net against potential failures. For example, integrating blockchain technology can enhance the traceability of votes, making it easier to audit election results without compromising the anonymity of the voters. Continuous investment in such innovations is critical for fostering secure electronic voting environments.
Best Practices for Secure Voting Procedures
To ensure the success of electronic voting systems, organizations must adopt best practices that incorporate both technological safeguards and procedural integrity. Robust verification processes, such as pre-election audits and post-election checks, can help verify that the voting process has been conducted without irregularities. Implementing such checks strengthens voters’ trust in the election outcomes.
Further, it is essential for organizations to conduct regular training for all involved in the voting process, from technical staff to trustees. These training sessions should cover best practices in key management, data security, and crisis management strategies to prepare for unforeseen challenges. By establishing a culture of security awareness, organizations can significantly diminish the risk of human error affecting election integrity.
The Future of Cryptographic Practices in Elections
Looking ahead, the future of cryptographic practices in elections seems promising as organizations prioritize the application of advanced technologies and enhanced protocols. Continuing to involve cryptographic research in the electoral process will facilitate innovative solutions that combat potential risks and improve overall election integrity. Emphasizing human factors in the design and implementation of these systems will be crucial in ensuring sustainable improvements.
Furthermore, fostering a collaborative environment where cryptographic researchers, voting officials, and technology developers can engage is key to navigating the complexities associated with electronic voting. This cooperation will contribute to developing robust systems that can prevent dilemmas similar to those faced by the IACR and ensure the future of secure elections.
Frequently Asked Questions
What are common cryptographic election flaws that can affect results?
Common cryptographic election flaws include encryption key loss, improper trustee key management, and issues within electronic voting systems like Helios. These flaws can prevent the accurate decryption of election results, as seen in the recent IACR election where a lost encrypted key halted the announcement of results.
How does encryption key loss impact election outcomes in cryptographic voting systems?
Encryption key loss can critically impact election outcomes by preventing access to the election results. For instance, in the IACR election, one trustee’s loss of their encrypted key made it technically impossible to decrypt the votes. This highlights the importance of proper key management in secure voting.
What is the role of trustee key management in securing cryptographic elections?
Trustee key management is vital in securing cryptographic elections as it involves distributing encrypted keys among multiple trustees to safeguard the voting data. If one trustee mismanages their key, as occurred in the recent IACR election, it jeopardizes the entire voting process, underscoring the need for robust protocols.
What lessons were learned from the IACR election and its cryptographic research implications?
The IACR election demonstrated the critical need for improved procedures in cryptographic research related to voting systems, particularly in key management. The organization plans to implement a ‘2-out-of-3’ threshold for private keys to enhance security and avoid future issues caused by human errors.
How do electronic voting systems like Helios enhance cryptographic security in elections?
Electronic voting systems like Helios enhance cryptographic security by encrypting votes to ensure confidentiality and integrity. They implement complex cryptographic protocols that require collaborative key management among trustees, essential for preventing flaws, such as those experienced in the IACR election.
What measures can organizations take to prevent cryptographic election flaws?
Organizations can prevent cryptographic election flaws by implementing strict trustee key management protocols, conducting regular training on key handling, utilizing robust electronic voting systems, and establishing clear written procedures. The IACR’s decision to adopt a ‘2-out-of-3’ threshold for key management illustrates a proactive approach to mitigating risks.
Why do cryptographic systems fail due to human errors in elections?
Cryptographic systems often fail in elections due to human errors such as mismanaging encryption key sharing or forgetting keys. Bruce Schneier emphasized that while these systems provide security, their effectiveness relies on human operation, which is inherently fallible, as exemplified in the IACR’s recent election challenges.
What actions did the IACR take after the failure in their cryptographic election?
After the failure in their cryptographic election, the IACR replaced the trustee who lost the encrypted key and announced a new election to be conducted under enhanced security measures, including a ‘2-out-of-3’ threshold for private key management, ensuring better protection against similar errors in the future.
| Key Points | Details |
|---|---|
| Election Results Cancellation | The IACR canceled the announcement of leadership election results due to a lost encrypted key. |
| Voting System | An electronic voting system requires three members to access encrypted results, with each holding a part of the key. |
| Cause of Error | One trustee lost their share of the encrypted key due to a human mistake, making it impossible to decrypt results. |
| New Election Plans | The IACR plans to conduct a new election and implement safeguards to prevent similar errors. |
| IACR Overview | The IACR, established in 1982, promotes research in cryptology and utilized an open-source voting system, Helios. |
| Human Factor | Failures in cryptographic systems are often attributed to human error, such as forgetting keys or mismanaging key sharing. |
| Current Voting Status | Voting has resumed and will continue until December 20, with a new trustee and improved key management procedures. |
Summary
Cryptographic election flaws became evident when the IACR had to cancel its leadership election results due to a lost encrypted key. This incident highlights the significant impact of human error on cryptographic systems, which are designed to offer security but can fail when not managed correctly. As a response, the IACR aims to enhance its voting processes with new safeguards and a clearer management system for encrypted keys, ensuring that future elections can be conducted successfully.